Running Github Advanced Security for Azure DevOps is easy task. You just need to add few tasks to your pipeline and that’s it. But what if you want to fail your pipeline when Ghazdo find vulnerability? It is not provided by default. In this article I will show you how to do this.
Github Advanced Security for Azure DevOps
GitHub Advanced Security for Azure DevOps is a comprehensive suite of security features that enhances the security of your development workflow while maintaining productivity.
Key Features
Secret Scanning helps detect any exposed secrets in your Azure Repos and prevents new secrets from shipping in your code1. It checks if code pushes include commits that expose secrets such as credentials2. It also scans your repository and looks for exposed secrets that were committed accidentally2.
Dependency Scanning identifies vulnerable open-source components you may be using1. It searches for known vulnerabilities in open source dependencies (direct and transitive)2. It provides straightforward guidance on how to update component references so you can fix issues in minutes1.
Code Scanning uses the CodeQL static analysis engine to identify code-level application vulnerabilities such as SQL injection and authentication bypass2. It helps you find and fix deep security vulnerabilities in your code without leaving Azure DevOps1.
GitHub Advanced Security for Azure DevOps integrates with Defender for Cloud to unify visibility of DevOps security posture, minimize blind spots within a single pane of glass, and get context-driven remediation guidance for code fixes1.
GitHub Advanced Security for Azure DevOps is priced at $49 per active committer per month and enables usage and invoice management through your Azure subscription1.
At this time, GitHub Advanced Security for Azure DevOps is only available for Azure DevOps Services and there are no plans to bring this product to Azure DevOps Server2.
How to run Ghazdo in Azure DevOps pipeline?
All what is needed is just a few tasks. Here is the example:
steps:
- checkout: self
- task: AdvancedSecurity-Codeql-Init@1
inputs:
languages: csharp
- task: AdvancedSecurity-Codeql-Autobuild@1
- task: AdvancedSecurity-Dependency-Scanning@1
- task: AdvancedSecurity-Codeql-Analyze@1
First we need to checkout our code. Then we need to initialize CodeQL. In this example we will analyze C# code. Next we need to build our code. Then we can run dependency scanning and code scanning.
There is no task for secret scanning which is done automatically. You can read more about this in the documentation.
But when you scan and vulnerability is found the pipeline will not fail. There is just warning which is easy to miss. So how to fail pipeline when Ghazdo find vulnerability?
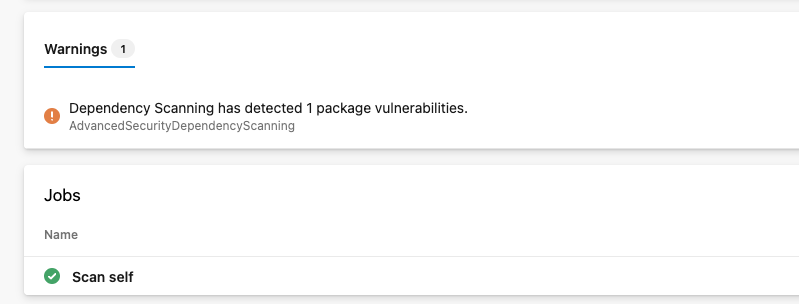
How to fail pipeline when Ghazdo find vulnerability?
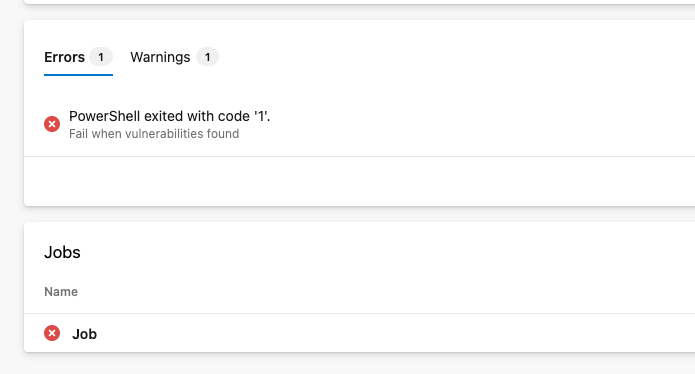
All what we need to do is to add one more task to our pipeline. This task will call GitHub Advanced Security for Azure DevOps API and check if there is any vulnerability. If yes then it will fail the pipeline. Here is the example:
- pwsh: |
$AccessToken = "Bearer $(System.AccessToken)"
$repoID = "$(Build.Repository.ID)"
$repository = "$(Build.Repository.Name)"
$teamProject = "$(System.TeamProject)"
$branchname= "$(Build.SourceBranchName)"
$url = "$(System.CollectionUri)"
#$organization=""
$regexPattern = "https:\/\/dev\.azure\.com\/([a-zA-Z0-9]+)\/"
$match = [regex]::Match($url, $regexPattern)
# Check if a match is found and extract the value
if ($match.Success) {
$organization = $match.Groups[1].Value
} else {
Write-Output "Organization no match found"
}
Write-Host "Repo ID: $repoID"
Write-Host "Repo Name: $repository"
Write-Host "Team Project: $teamProject"
Write-Host "Branch Name: $branchname"
Write-Host "Organization: $organization"
# Call the adv security dependecies
$dependenciesURL = "https://advsec.dev.azure.com/$($organization)/$($organization)/_apis/Alert/repositories/$($repository)/Alerts?top=50&orderBy=severity&criteria.alertType=1&criteria.ref=refs/heads/$($branchname)&criteria.states=1"
Write-Host "Dependencies URL: $dependenciesURL"
$response = Invoke-RestMethod -Uri $dependenciesURL -Headers @{Authorization = $AccessToken} -ContentType "application/json" -Method Get
Write-Host "Response: $response"
$dependencies = $response.value | Where-Object { $_.severity -eq "critical" }
# check the json for high vulnerabilties
if ($($dependencies.Count) -gt 0)
{
Write-Host "Found [$($dependencies.Count)] critical vulnerabilities in the branch" -ForegroundColor Red
exit 1
}
else
{
Write-Host "No critical vulnerabilities in the branch"
}
displayName: 'Fail when vulnerabilities found'
With this task you can tailor your pipeline to your needs. You can fail pipeline when there is any vulnerability or just when there is critical vulnerability. You can also fail pipeline only for specific branch.
Please share in comments how you do you use GitHub Advanced Security for Azure DevOps. Do you allow to merge pull request when there is vulnerability? Do you fail pipeline when there is vulnerability?


Comments